What Is Com Sec Enterprise Knox Cloudmdm Smdms App?

Welcome! You’ve probably heard about Mobile Device Management (MDM) and its importance in today’s world where devices are essentially extensions of ourselves. But have you come across com.sec.enterprise.knox. clouded.smdms? If not, you’re in for a treat! This tool is an integral part of Samsung Knox, a robust suite of mobile device management solutions that lets you easily control and protect your company’s devices.
Also Read: What Is IMS Service And How To Fix The Has Stopped Problem?
This article’ll delve into the details of com.sec.enterprise.knox.cloudmdm.smdms. We’ll explain how to use it, its security features, device management capabilities and how it integrates with other tools and platforms. We’ll also share some successful case studies, common issues and troubleshooting tips. Plus, we’ll give you a sneak peek into future developments and updates. So buckle up; by the end of this guide, you’ll be well on your way to mastering this powerful MDM solution!
Overview of Mobile Device Management (MDM)

You’ve probably heard about Mobile Device Management (MDM), but are you aware of its growth and development over time? MDM’s evolution has been fascinating, transforming from a basic tool for business mobile devices to a comprehensive solution for managing all enterprise mobility needs. It’s equipped with features and tools like device tracking, app distribution, data security, and much more that can effectively streamline your organization’s operations.
Brief history and development
Over the years, the development and evolution of Enterprise Knox CloudMDM has been remarkable. Since the Knox inception, numerous milestones have marked its growth and expansion into a leading Mobile Device Management (MDM) solution. What began as a simple concept to manage mobile devices within an organization has become a powerful tool that caters to thousands of businesses worldwide. Each evolution milestone represents an improved version, often with enhancements and new features offering more robust security measures and easier device management capabilities.
From its early days of simply providing basic functionalities like enforcing passcodes and remote wipe, to now offering complex tools such as data encryption, application management, secure containerization, and VPN configurations; we’ve seen an impressive growth in its functionality range. These advancements reflect changes in technology and shifts in organizational needs for managing their digital assets securely. Now let’s dive deeper into these features and tools offered by Enterprise Knox CloudMDM that make it such an efficient MDM solution today.
Overview of its features and tools
Like a master key unlocking the full potential of mobile device management, Enterprise Knox CloudMDM’s suite of features and tools are designed to safeguard and streamline your organization’s digital operations. Its robust feature customization options allow you to tailor your mobile device management approach to your needs. You can set rules for data usage, configure VPN settings, enforce security protocols and much more. The platform’s tools also offer exceptional usability – they’re designed to be intuitive so that even non-technical staff can easily manage devices.
In addition to its flexibility and user-friendly interface, Enterprise Knox CloudMDM has advanced functionalities to enhance security and productivity. Take a look at the following table showcasing some remarkable features:
| Security Enhancements | Productivity Boosters |
|---|---|
| Comprehensive Data Protection | Efficient Device Management |
| Robust Malware Defense | Streamlined App Deployment |
These powerful capabilities not only foster a secure environment but also create conditions conducive for efficient workflows. With such an impressive array of features and tools within Enterprise Knox CloudMDM’s arsenal, you’re well-equipped in navigating the complexities of mobile device management. Next up: let’s delve into a more detailed exploration of what com.sec.enterprise. Knox. clouded.smdms has in store for you.
Detailed Look at com.sec.enterprise.knox.cloudmdm.smdms
Diving into the specifics, com.sec.enterprise.knox.cloudmdm.smdms is integral to Samsung Knox’s mobile device management (MDM) solution. It offers a robust platform that allows IT admins to manage and control enterprise devices efficiently. But just like any other program, it faces competition from similar products in the market such as IBM MaaS360, VMWare AirWatch, and MobileIron. These competitors offer similar features but differ in their implementation and user interface.
While you find com.sec.enterprise.knox.cloudmdm.smdms quite advantageous for your business needs, it’s also important to be aware of its potential limitations. One of these could be the fact that it is specifically designed for Samsung devices which might limit its usage if you have a diverse range of devices within your organization. Additionally, while Samsung advertises seamless integration with their own suite of services and applications, interoperability with third-party apps or systems may not always be as smooth.
As we proceed further into this discussion on com.sec.enterprise.knox.cloudmdm.smdms, it’s essential to recognize the importance of understanding how to utilize this tool given these considerations effectively. We’ll delve deeper into how one can optimize its use for managing enterprise mobile devices next.
How to Use com.sec.enterprise.knox.cloudmdm.smdms
Are you ready to maximize the use of com.sec.enterprise. Knox. clouded.smdms? We’ll guide you through its setup and configuration process, ensuring everything is perfectly in place. Additionally, we’ve prepared a user guide to help you navigate this application smoothly and efficiently.
Setup and configuration
Setting up and configuring your Enterprise Knox CloudMDM couldn’t be simpler, but it’s a game-changer for managing your business’ mobile devices. With its cloud-based functionality, you can easily control and secure all of your mobile devices from one central location. The device enrollment process is straightforward; you need to register the device on the platform. This allows you to simultaneously implement security measures, distribute apps, and manage updates across multiple devices.
Once everything is set up properly, the benefits of this system become apparent quickly. It’s convenient and enhances overall productivity by ensuring that all mobile devices within your organization are running optimally and securely. Now that we’ve covered setup and configuration, let’s delve into how to make the most of these features using our user guide.
User guide
Navigating the user guide is as easy as pie, and it’s packed with every tiny detail you could possibly need to master your mobile device management. Use this manual to gain a comprehensive understanding of all features and capabilities of the Knox Cloud MDM solution, from setting up devices to monitoring them in real time. Don’t shy away from exploring it in depth; it will provide valuable user training and help you troubleshoot any issues that might arise.
Remember, a well-informed user is an empowered one so take advantage of this resource. The guide also presents an opportunity for you to share your experiences and give user feedback on how the system can be improved or what additional support may be needed. This two-way communication channel helps enhance product development and customer satisfaction simultaneously. Now that you’re fully versed on how to utilize the guide and its benefits, let’s delve deeper into understanding the security features associated with Knox Cloud MDM for optimal protection of your mobile data ecosystem.
Understanding the Security Features
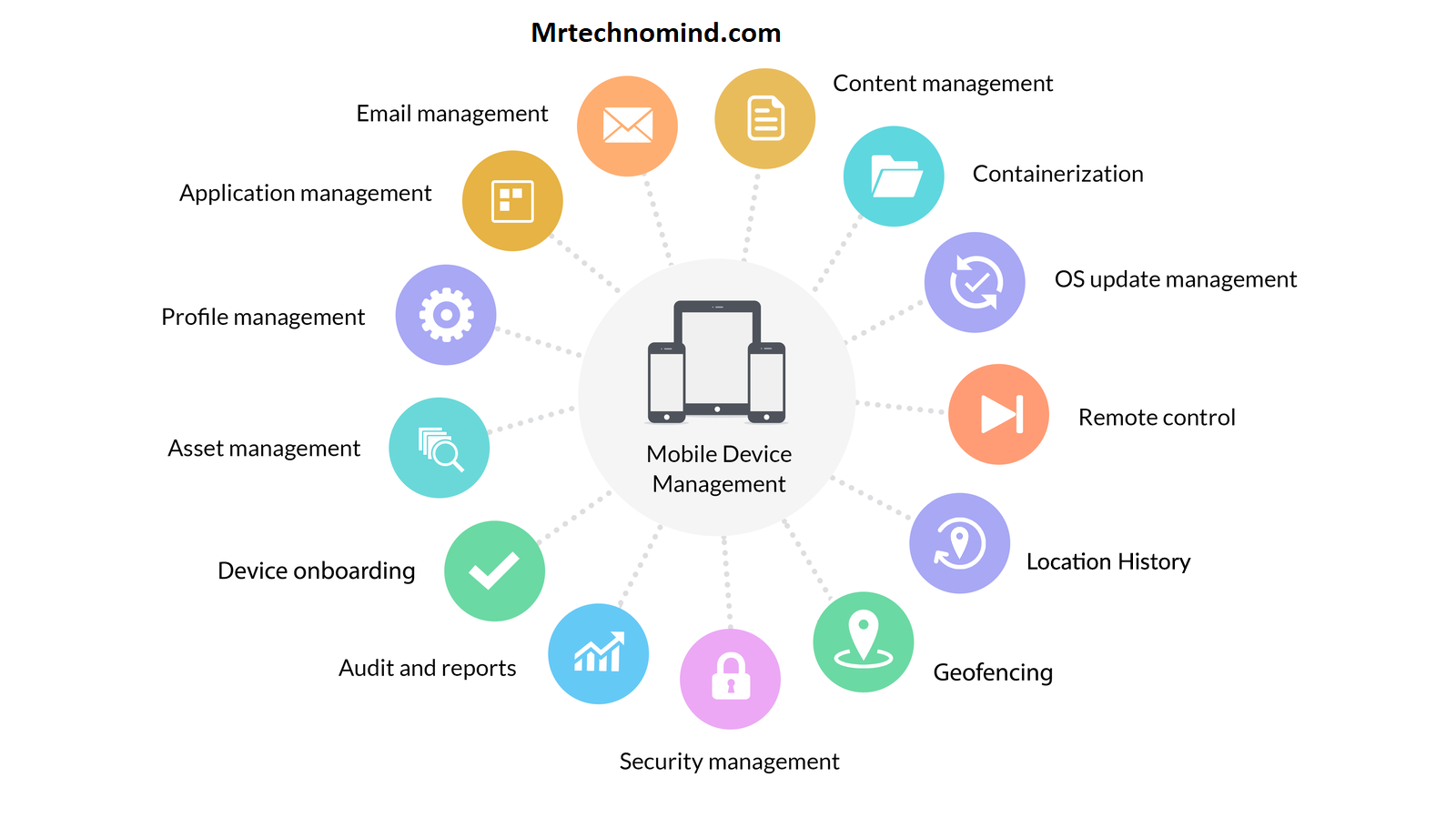
In this discussion, we’ll dive into the security features of com.sec.enterprise.knox.cloudmdm.smdms. You’ll get a thorough understanding of its data protection capabilities ensuring your sensitive information is well safeguarded. We’ll also delve into user authentication and access control mechanisms, showing how this tool maintains strict boundaries on who can access the data.
Data protection capabilities
You’ll be amazed at the robust data protection capabilities offered by COM.SEC.enterprise.knox. clouded.smdms, as it ensures your sensitive information remains secure and inaccessible to unauthorized individuals. The platform uses sophisticated data encryption methods that convert your sensitive business data into complex codes. These codes are nearly impossible for hackers to decipher, providing an extra layer of security. In addition, this system has been designed with full consideration of the impact posed by stringent privacy legislation, ensuring that you remain compliant while maintaining high data protection.
Beyond these impressive features, COM.SEC.enterprise.knox.cloudmdm.smdms offers more than just encryption; it also provides essential tools for managing access and user authentication. This means you can limit who gets access to what information, further bolstering security measures. Consequently, this protects your critical business data from external threats and reduces risks within your organization. With such a comprehensive approach to securing your enterprise’s vital assets in place, let’s delve deeper into how the system manages user authentication and access control.
User authentication and access control
Let’s talk about user authentication and access control – two critical aspects of any robust data protection strategy. One powerful method you can use is Biometric Security, which uses unique physical or behavioral characteristics such as fingerprints, facial recognition, or iris scan to verify a user’s identity. This adds an extra layer of security because biometric data cannot be easily duplicated or stolen compared to traditional passwords. Another effective way is Multi-factor Authentication (MFA). MFA requires users to present two or more forms of identification before gaining access to sensitive information. This could be something they know (like a password), something they have (like a smart card), and something they are (biometrics).
The combination of biometric security and multi-factor authentication makes it extremely difficult for unauthorized individuals to access your valuable data. Not only do these methods provide strong security measures, but they also offer streamlined processes that don’t overly inconvenience authorized users. While focusing on securing the front door with robust user authentication techniques is crucial, remember that device-level security controls are equally important too. So next up, let’s dig deeper into how you can further fortify your defenses with device management capabilities.
Device Management Capabilities

Let’s delve into the capabilities of device management. Picture having the power to control your devices remotely and easily manage their policies. These features offer you an unprecedented level of control and security, ensuring that managing your devices is not just efficient, but also incredibly secure.
Remote device control
With remote device control, you’re able to manage your devices from anywhere in the world, making it easy and convenient for your business. However, as advantageous as this capability may be, it’s important to understand and respect remote access limitations. Respecting these restrictions is not just about compliance but also about practicing good device control ethics. You should always ensure that any access or changes made to a device are done with permission and for legitimate business reasons.
In managing your devices remotely, one key aspect to pay attention to is setting up appropriate policies for use. This will help you maintain ethical standards while leveraging remote control capabilities’ benefits. It’s all about balancing operational efficiency and user privacy rights. Moving forward, let’s delve deeper into how you can effectively set up and enforce these crucial device policy management guidelines within your organization.
Device Policy Management
Drawing parallels to the wise old proverb, ‘Give a man a fish and you feed him for a day; teach a man to fish and you feed him for a lifetime,’ taking charge of your device policy management is like setting up the fishing rod for your organization’s digital safety. Think of policy enforcement strategies as the bait that lures in secure behavior and compliance monitoring techniques as the line that ensures no security risks slip away unnoticed. By articulating clear policies and consistently enforcing them, you establish guidelines and create an environment where safe practices become second nature. Just as one cannot catch fish without understanding their habits and habitats, successful device policy management requires thorough knowledge about potential threats and how to counteract them.
Consider compliance monitoring techniques as your eyes on the water in this context. These tools help you keep track of whether devices adhere to set policies or if there are any deviations which could pose risk. This way, immediate actions can be taken before minor issues escalate into major complications. It’s not just about laying down rules; it’s about ensuring those rules are followed diligently while being prepared for possible breaches at all times. On that note, let’s delve deeper into how device policy management goes hand-in-hand with various other tools and platforms enhancing overall system integrity.
Integration With Other Tools and Platforms
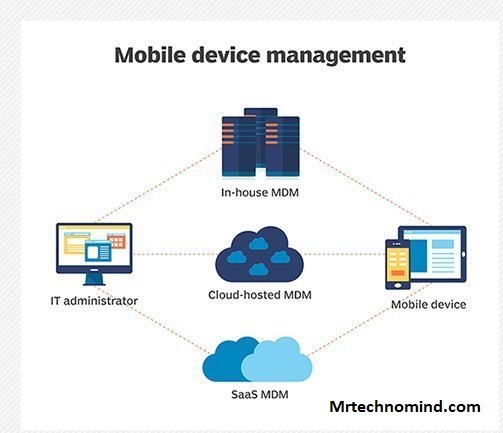
Let’s dive into how Samsung Knox integrates with other tools and platforms. You’ll find that it’s compatible with other Samsung Knox tools and smoothly integrates with third-party applications. This interoperability brings about a more streamlined, efficient device management system, so let’s explore this in more detail.
Compatibility With Other Samsung Knox Tools
You’ll be thrilled to know that Com.Sec.Enterprise.Knox.CloudMDM.SMdmS is fully compatible with other Samsung Knox tools, offering you a seamless and efficient user experience. This compatibility ensures swift Knox tools integration, which lays the foundation for centralized control of all your Samsung devices under one platform. The CloudMDM advantages are manifold; not only does it enhance device management, but it also bolsters security and simplifies administrative tasks.
In addition to being integrated with Samsung’s suite of Knox tools, this comprehensive solution is designed to work in harmony with a multitude of third-party applications as well. This flexibility allows you to leverage the best features from varied software solutions without compromising on ease-of-use or efficiency. So, let’s take a closer look at how this integration with third-party applications can revolutionize your mobile device management strategy.
Integration With Third-party Applications
Having explored how seamlessly Samsung’s Knox CloudMDM can interoperate with other tools within the Knox ecosystem, let’s now focus on another key aspect – its integration capabilities with third-party applications. This feature is particularly important because it expands the functionality of Knox CloudMDM beyond just device management and offers businesses a way to maximize their existing software investments.
Third party compatibility and application interfacing are areas where Knox CloudMDM truly shines. Here are three reasons why:
- It allows for greater flexibility: You aren’t restricted to using only Samsung’s suite of enterprise solutions. Instead, you can directly integrate your favorite productivity or security apps into the system.
- It leads to improved efficiency: Your team doesn’t need to switch between different platforms or systems; everything they need can be accessed from one place.
- It enhances cost-effectiveness: Integrating existing software reduces the need for additional investments in new platforms.
As a result, you gain access to robust mobile device management features and create an all-in-one solution that caters specifically to your business needs. Now that we’ve unpacked these benefits, let’s take a closer look at some real-world examples where companies have leveraged this powerful capability effectively in our next section on case studies of successful implementation.
Case Studies of Successful Implementation

Dancing in the spotlight of success, several organizations have painted a masterpiece on the canvas of their operational efficiency through successfully implementing Samsung’s Knox CloudMDM solution. Despite facing numerous implementation challenges, these companies demonstrated resilience and adaptability. The initial roadblocks included integration issues with existing systems, technical glitches during rollout, and staff training for optimum utilization.
One such example is that of a multinational corporation which managed to overcome these obstacles by deploying a phased roll-out strategy, allowing them to tackle each challenge head-on while minimizing risk. They started small – first implementing in non-critical departments before scaling up to more sensitive areas. This approach allowed them to gather feedback, make necessary adjustments and ensure seamless transition across all units. Their success metrics included increased productivity due to reduced downtime, improved data security compliance rates and positive user feedback regarding ease of use.
However, even the most successful implementations aren’t without their quirks and hitches – it’s part of the journey towards digital transformation. It’s important to remember that every organisation has unique needs and circumstances; hence there isn’t a one-size-fits-all solution or a guarantee against occasional difficulties cropping up post-implementation. Henceforth we discuss common issues encountered during usage along with effective troubleshooting techniques that can act as your lifeline when navigating this technological sea.
Common Issues and Troubleshooting
So, you’ve implemented an enterprise mobility management system but are now facing some issues? Don’t worry, it’s not uncommon to encounter a few bumps on the road. This section’ll delve into typical problems and provide solutions and fixes to ensure your system continues operating smoothly.
Typical Problems Encountered
You might wonder what challenges you could face when implementing Samsung Knox Cloud MDM. It’s not uncommon to encounter a few bumps, ranging from minor glitches to major operational issues. Problem diagnosis and solution implementation can sometimes be tricky, especially without proper guidance or technical know-how. You may run into problems like failed device enrollment, issues with policy application, connectivity troubles, or even app management difficulties.
While these issues sound intimidating, remember that they’re typical challenges that many users face. With patience and a systematic approach to problem-solving, you’ll soon get your enterprise back on track. Don’t let these hurdles discourage you; use them as learning opportunities to understand the platform’s intricacies better. Now let’s move forward and delve deeper into how we can effectively address these issues through practical solutions and fixes.
Solutions and Fixes
Tackling these issues head-on, let’s explore some effective solutions and quick fixes that can help smooth out any bumps you may encounter while using Samsung Knox Cloud MDM. One solution is to investigate Knox CloudMDM Alternatives. Just like with any other software, sometimes a different approach or system might suit your needs better. So don’t be afraid to look around and try out different services before settling on the one that works best for you.
Performance Optimization is another key area where you can make improvements. Regular updates and maintenance checks can ensure your system remains efficient and reduces the chances of facing technical difficulties or glitches. Ensure all your devices are up-to-date with the latest software versions as outdated versions often lead to incompatibility issues causing malfunctions. Through these measures, you’ll solve current challenges and prevent potential future ones too! Now, let’s dive into what lies ahead: The exciting world of future developments and updates within the realm of Samsung Knox Cloud MDM.
Future Developments and Updates

It’s crucial to know what’s coming next with Samsung Knox. You can anticipate new features and improvements in upcoming versions that will further enhance your device management capabilities. Keep track of updates and regularly check for announcements so you’re always leveraging the latest advancements.
What to Expect in Upcoming Versions
Excitement’s building as we await the upcoming versions of COM.SEC.Enterprise.Knox.CloudMDM.SMDMS, promising an array of advanced features and improved functionalities. The version anticipation is palpable in the tech community, as developers and users alike eagerly look forward to these advancements. It’s expected that these future releases will continue to leverage innovation, enhancing user experience with smoother operations and more robust security measures. Upcoming enhancements will likely include improvements in device management capabilities, strengthened data protection protocols, and streamlined cloud integration processes.
While imagining the potential changes is exciting, it’s equally important to keep up-to-date with all the latest updates. To do this effectively, subscribe to their newsletters or regularly check their official website for announcements. What’s next? Let’s delve into navigating through updates without missing anything crucial.
How to Stay Updated
Navigating the sea of updates doesn’t have to be overwhelming, and there’s a straightforward way to stay in the loop. The first step is to adopt some staying informed strategies that suit your needs and lifestyle. For instance, you might choose to receive newsletters or email updates directly from com.sec.enterprise.knox.cloudmdm.smdms. Alternatively, you could follow their social media channels for real-time information or even join user forums where other users share insights on new features and improvements.
In addition to these tactics, it’s smart to keep an eye on the latest technology trends relevant to cloud-based mobile device management systems. This will help you anticipate what might be coming down the pipeline and enable you to maximize use of existing features within the platform. Remember, being proactive about staying informed can make all the difference when it comes to navigating changes smoothly and effectively.
Frequently Asked Questions
What is the Cost of Using Com.sec.enterprise.knox.cloudmdm.smdms?
Imagine you’re on a voyage, sailing through the vast sea of digital management services. As you navigate these waters, you stumble upon com.sec.enterprise.knox. Clouded.smdms. Your provided context does not mention the cost of using this service. However, like most cloud-based services, it likely involves a subscription fee. The Subscription Benefits of this service are manifold and can include centralized control over multiple devices and streamlined device management among others. Not to mention the robust Security Features it offers such as data encryption and stringent access controls that act as the armored hull of your ship in this metaphorical digital sea, safeguarding your enterprise’s sensitive data against potential threats.
Is There a Free Trial Version Available for Com.sec.enterprise.knox.cloudmdm.smdms?
Sure, you want to know if a free trial version for com.sec.enterprise.knox.cloudmdm.smdms is available. It’s not explicitly mentioned on their website whether they offer a free trial. However, companies often provide limited access or functionality during trials to give potential users a taste of the user experience before making a full commitment. These are known as ‘Trial Limitations’. It’s always best though to reach out directly to the company for the most accurate and up-to-date information regarding free trials and any associated limitations.
How Does Com.sec.enterprise.knox.cloudmdm.smdms Compare to Other Similar Tools on the Market?
Imagine a solid and secure fortress with advanced defense mechanisms that make it one of the strongest in its realm. That’s what com.sec.enterprise. Knox.cloudmdm.smdms feels like compared to similar tools on the market. Its robust security features are its crowning glory, designed to protect your enterprise data like a steadfast guard. It’s not just about safety, though – this tool also has superior integration capabilities. Picture the smooth flow of rivers merging into an ocean; that’s how seamlessly it integrates within your IT infrastructure. So when you’re weighing up options for mobile device management solutions, remember: not all fortresses are built alike – some stand tall and unmatched like com.sec.enterprise.knox. clouded.smdms.
Does Com.sec.enterprise.knox.cloudmdm.smdms Offer Support for Non-technical Users?
Yes, com.sec.enterprise.knox.cloudmdm.smdms is designed with a user-friendly interface that makes it accessible even to non-technical users. You’ll find its features easy to navigate and understand, making it simple for you to take full advantage of what it offers. The tool also includes accessibility features that ensure everyone can use it effectively and efficiently, regardless of their technical skills or capabilities. It’s all about simplifying the process for you and providing support whenever you need it.
Are There Any Specific System Requirements for Using Com.sec.enterprise.knox? Clouded. Smdms?
You’re probably wondering, “What do I need to use com.sec.enterprise.knox. clouded.smdms?”Hold on to your seat because it’s less complicated than you think. First things first, device compatibility plays a crucial role. The beauty of this software is that it’s designed to work seamlessly across various devices – be it smartphones, tablets or computers. But remember, the implementation process isn’t just about installing the software on your device; there are other factors at play too such as network requirements and security protocols. So before diving in, ensure your systems meet all these requirements to ensure a smooth sailing experience with com.sec.enterprise.knox.cloudmdm.smdms.
Conclusion
So, you’ve ventured into the realm of mobile device management with com.sec.enterprise.knox.cloudmdm.smdms. It’s a mouthful, isn’t it? But don’t let that intimidate you. This powerful tool provides security features and management capabilities that can transform your business operations.
Remember, Rome wasn’t built in a day. It may take time to integrate and troubleshoot this system fully. But as future developments roll out, you’ll be at the forefront of MDM technology, ready to conquer any challenge thrown your way!